UWSP Pointer Overflow CTF
目录
Misc
Sight Without Vision
Here You See A Passer By
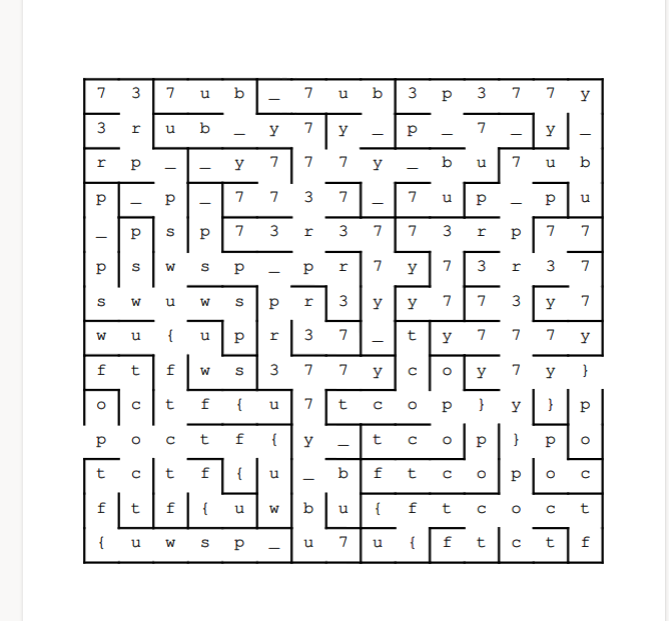
走迷宫
1 | poctf{uwsp_pr377y_bu7_p377y_bu7_pr377y} |
Steg
Absence Makes Hearts Go Yonder
给了gif
flag在文件末尾
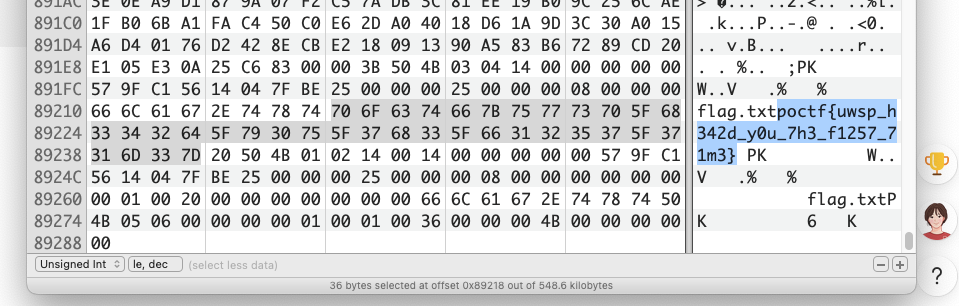
1 | poctf{uwsp_h342d_y0u_7h3_f1257_71m3} |
An Invincible Summer
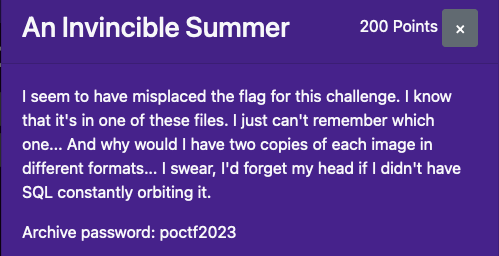
给了很多图片,每个图片都有两种格式,双图隐写考虑合并
随便取两张图,在sub下看到了相对奇怪的红点

保存提取,发现明文
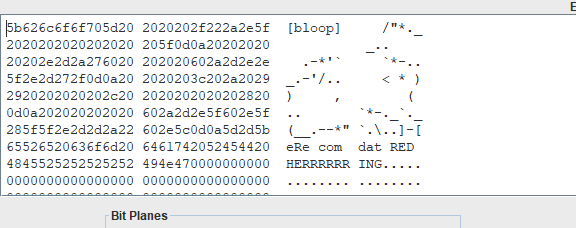
于是写脚本来提取
1 | import os |
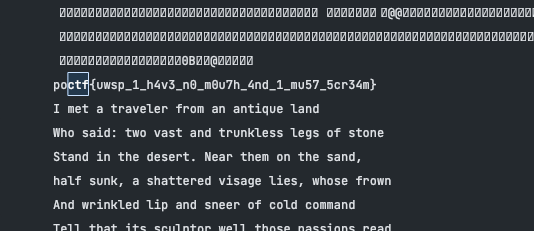
Between Secrets and Lies*

Web
We Rest Upon a Single Hope
前端题
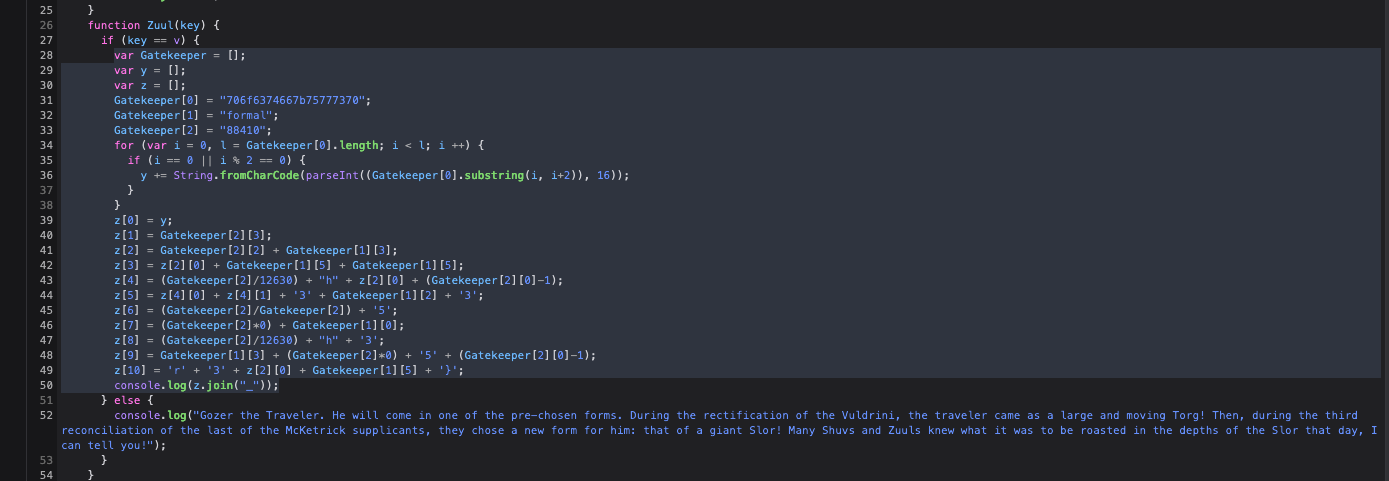
跑一下就出来了
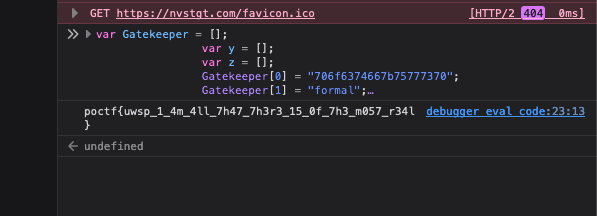
1 | poctf{uwsp_1_4m_4ll_7h47_7h3r3_15_0f_7h3_m057_r34l} |
Vigil of the Ceaseless Eyes
一个论坛
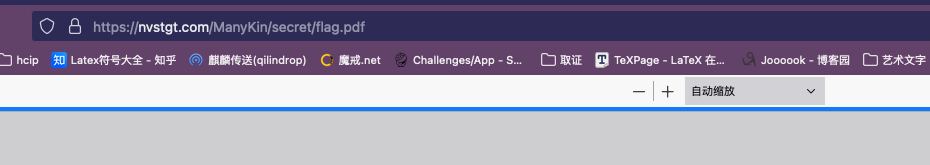
直接访问即可
1 | poctf{uwsp_71m3_15_4n_1llu510n} |
Quantity is Not Abundance
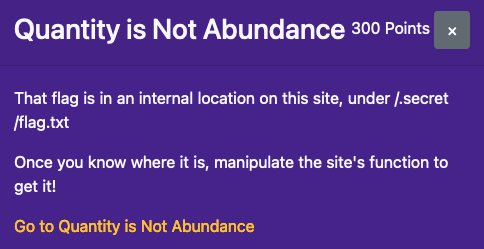
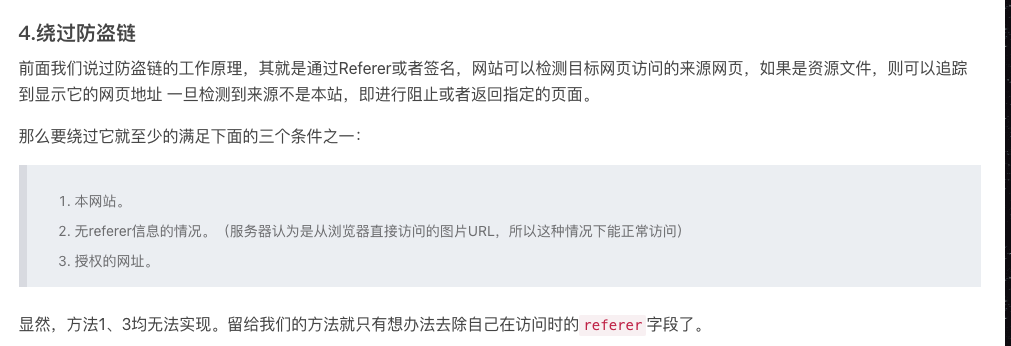
加上Referer即可
1 | Referer: https://nvstgt.com/Quantity/index.html? |
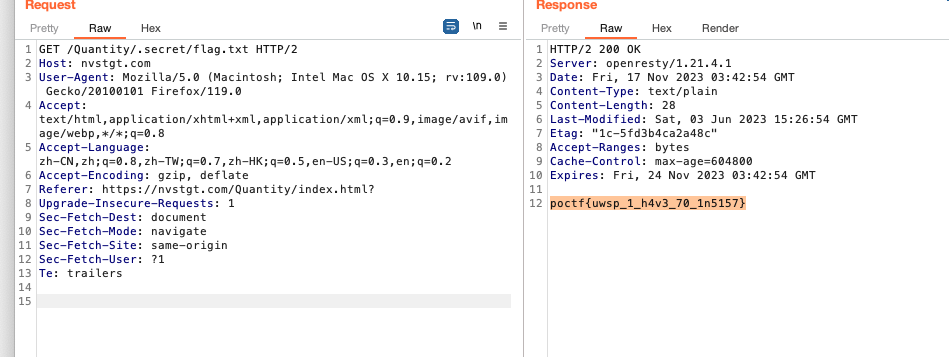
1 | poctf{uwsp_1_h4v3_70_1n5157} |
Crypto
Unquestioned and Unrestrained
base64
1 | poctf{uwsp_411_y0u2_8453_423_8310n9_70_u5} |
A Pale, Violet Light
1 | e= 5039 |
RSA
1 | from Crypto.Util.number import long_to_bytes,inverse |
Missing and Missed
brainfuck
1 | ++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>++++++++++++.-.------------.+++++++++++++++++.--------------.+++++++++++++++++++++.------.++.----.---.-----------------.<<++++++++++++++++++++.-.++++++++.>>+++++++++.<<--.>>---------.++++++++++++++++++++++++.<<-----.--.>>---------.<<+++++++++.>>---------------.<<---------.++.>>.+++++++.<<--.++.+++++++.---------.+++++++..----.>>++++++++.+++++++++++++++. |
Crack
We Mighty, We Meek*
excel密码爆破
1 | office2john crack1.xls > hash.txt |
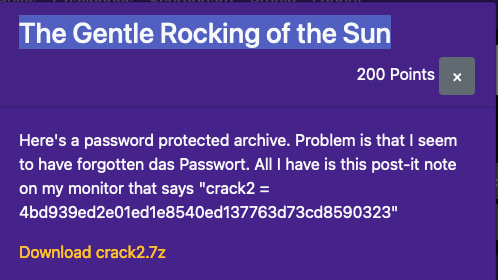
The Gentle Rocking of the Sun
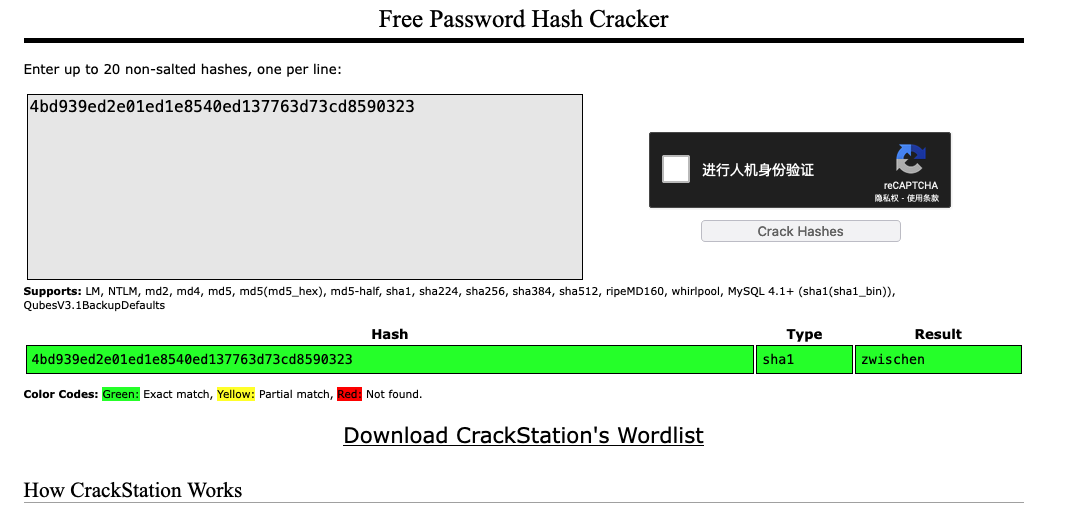
1 | zwischen |
解压出来还是个嵌套的文件夹
1 | import os |
With Desperation and Need*
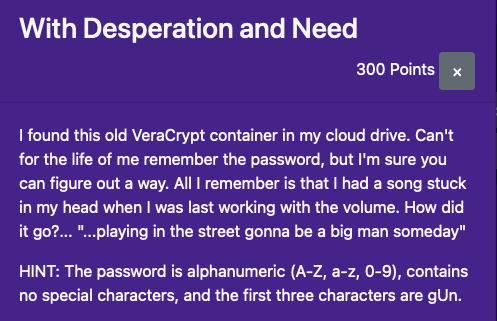
veracrypt加密卷爆破密码
Reverse
Easy as it Gets
1 | [Reflection.Assembly]::LoadWithPartialName("System.Security") |
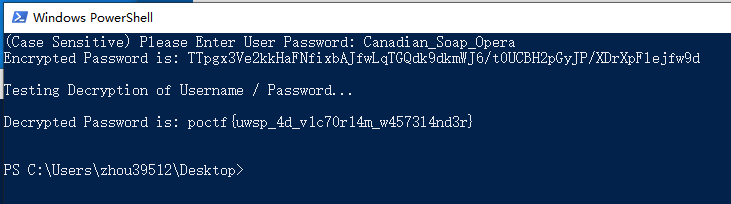
1 | poctf{uwsp_4d_v1c70r14m_w4573l4nd3r} |
A Tangled Web We Weave
1 | section .data |
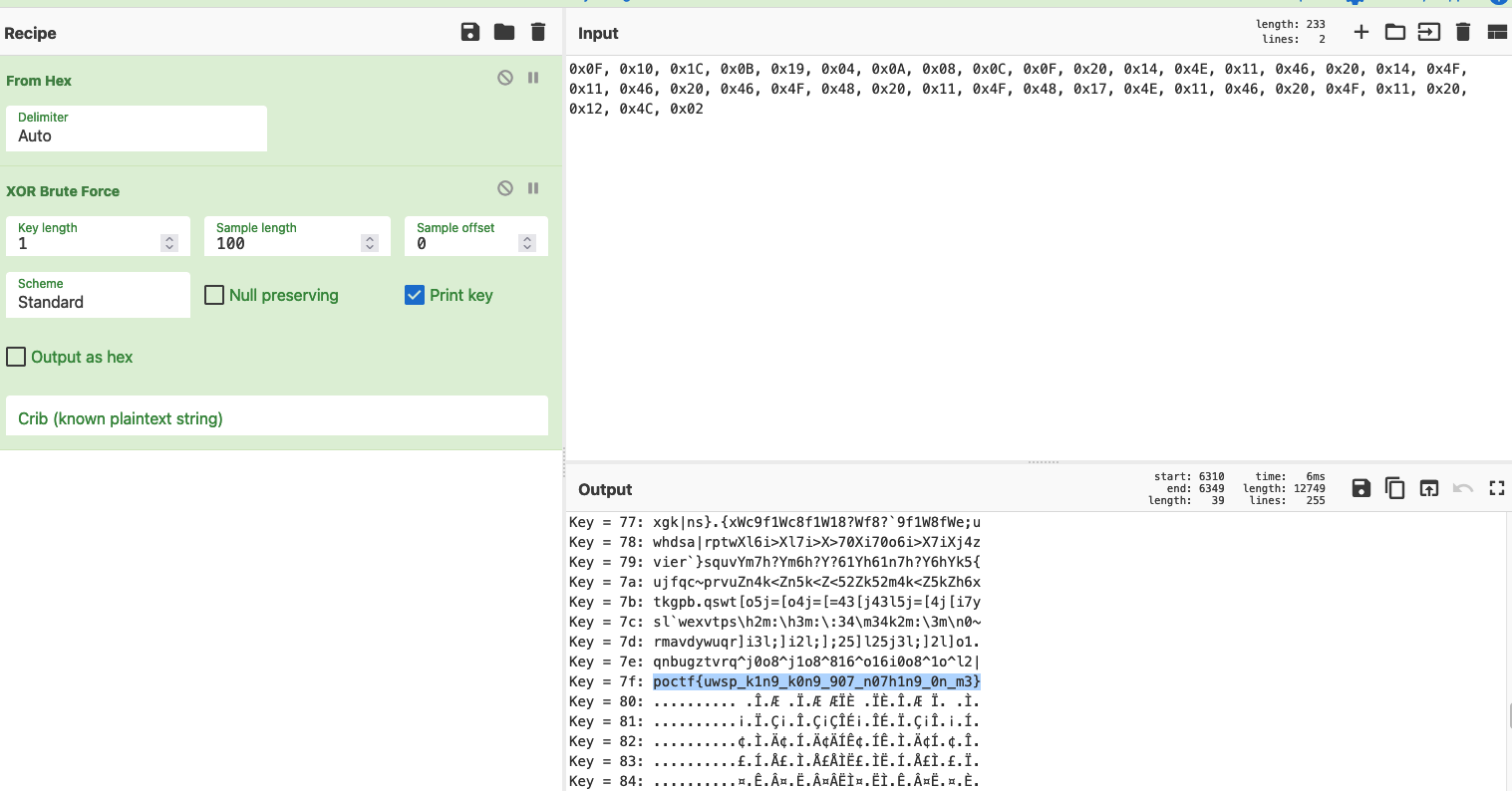
一眼异或加密
1 | poctf{uwsp_k1n9_k0n9_907_n07h1n9_0n_m3} |
Sunshine on Filth is Not Polluted
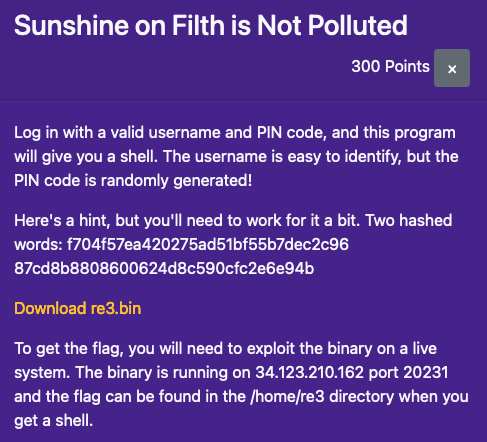
hint为
1 | Uninitialized variables |
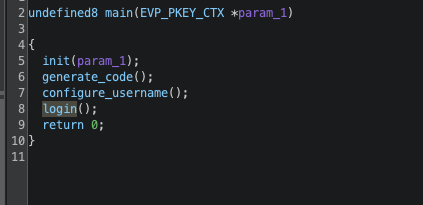
在login里面可以得到shell
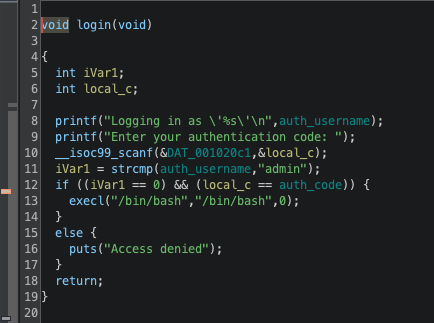
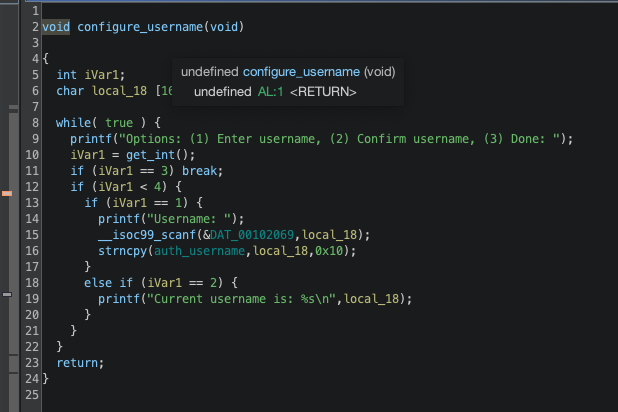
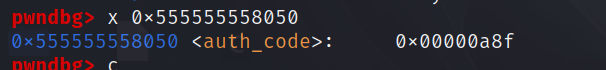
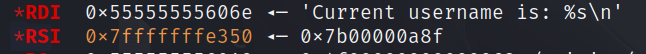
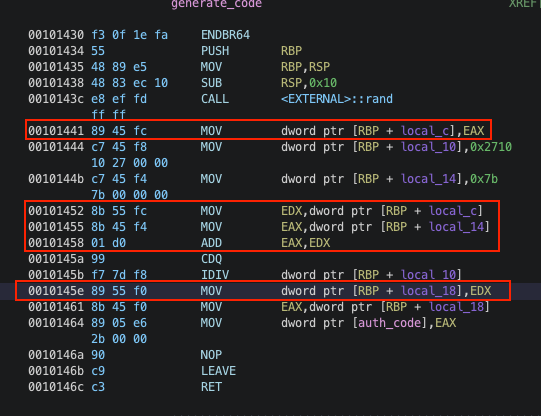
authcode是随机生成的
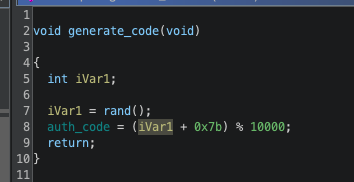
这里的confire username的username是没有初始化的,而且调试发现恰好此时local_18就是之前残留的auth_code的值
所以exp如下
1 | from pwn import * |
Forensics
If You Don’t, Remember Me
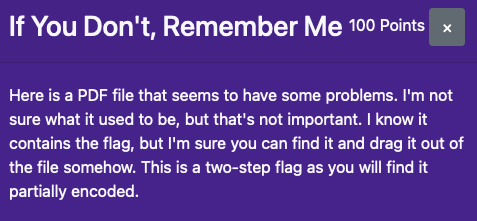
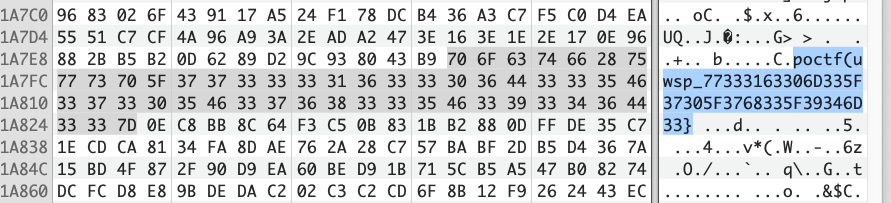
1 | poctf{uwsp_w31c0m3_70_7h3_94m3} |
A Petty Wage in Regret
给了一张图片

图片锐度明显有问题

第一部分在exif信息的ascii里
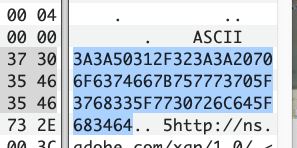
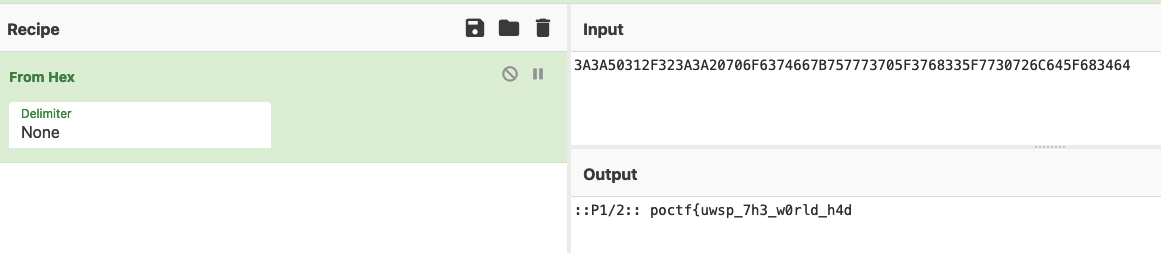
1 | poctf{uwsp_7h3_w0rld_h4d_17_f1257} |
Better to Burn in the Light
从磁盘文件中恢复文件
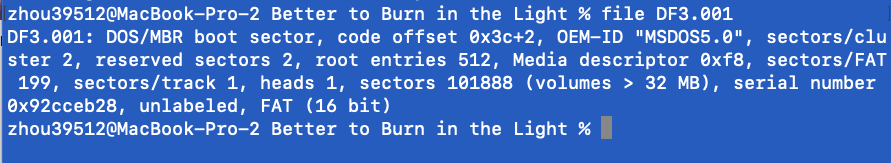
Master File Table
binwalk可以得到第一个flag
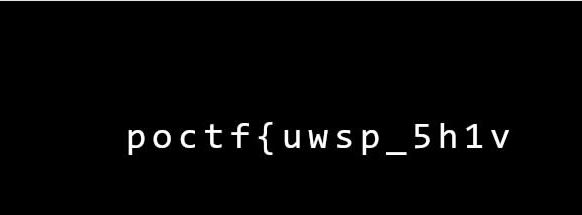
通过exif信息中的CLUE,可以找到第二张图


1 | poctf{uwsp_5h1v3r_m3_71mb3r5} |
Exploit
随便做了一道后面没做了
My Friend, A Loathsome Worm
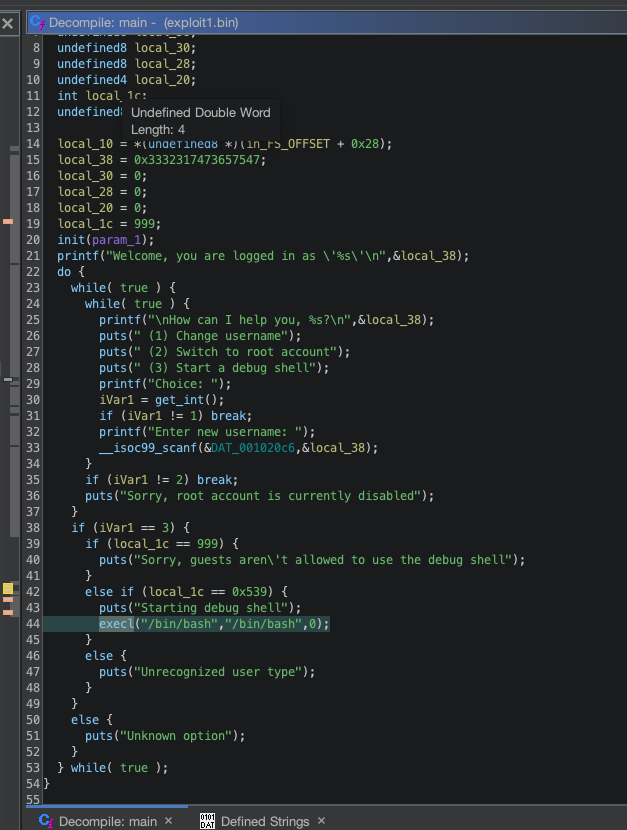
在输入username的地方溢出,将loacl_1c的位置覆盖为0x539即可
1 | from pwn import * |